Introduction
Network devices form the bedrock of networking infrastructure. The most basic network consists of at least two computing devices (laptops, phones, tablets, etc) connected by a medium (wires, Wi-Fi, Bluetooth, infrared, etc) so that the two devices can exchange data. More complex networks will include other networking devices that will help transmit data between multiple devices. This blog will explore some of the common networking devices, and their functions or uses within the network. It will also discuss how well each device fits in a modern network.
Knowledge of what various devices do is an essential component of understanding the basis of networking fundamentals.
What are Networking Devices
Networking devices are components of a network that help facilitate communications between devices. They are typically hardware devices that participate in running different networking protocols. Examples of networking devices are routers, switches, bridges, hubs, firewalls, etc. These devices operate at the different levels of the OSI model and are the foundation of building a network infrastructure.
Common Networking Devices
Some common networking devices you should be familiar with as a beginner in a networking or IT career are as follows;
- Network Repeaters (Repeaters)
- Hubs
- Bridges
- Switches (including Multilayer Switches)
- Routers
- Modems
- Firewalls
- Network Interface Cards
1. Network Repeater
Repeaters are network hardware that receives electrical, optical, or wireless signals from a source, amplifies the signal, and then transmits them to another destination. They operate at the physical layer of the OSI model (Layer 1). Normally, when a signal travels through a physical medium such as through an ethernet cable or through Wi-Fi, it gets weakened by a process called attenuation. A repeater functions to increase the strength of such a signal by repeated amplification as it traverses from one point to another. Repeaters can therefore be used to increase the distance that a signal travels without degradation.

Repeaters for Ethernet cables are not much in use today. In Wi-Fi networks, Wireless Wi-Fi Repeaters are very useful in extending the range of the Wi-Fi signals. Wi-Fi Extenders are similar to Wi-Fi Repeaters in their use but they differ in the sense that they create a new network by using a wired connection with a router. Optical repeaters (or optical amplifiers) are in use in fiber-optic cables to amplify and retransmit depleted signals.
How Does A Repeater Work?
A repeater is a dumb device that basically receives a signal from a particular interface or port, amplifies the signal, and then sends it out through another interface or port. A repeater will simply rebroadcast the amplified signal without making any intelligent decision such as separating the signals into different VLANs (Virtual Local Networks).
When To Use Repeaters
Older ether ethernet repeaters are rarely in use in enterprise networks. Wifi-Repeaters are common in many networks. The main uses of repeaters are as follows;
- To increase the signal range over a longer distance. The more the number of repeaters, the greater the distance the signal can travel until it is no longer feasible.
- Repeaters are used to overcome physical barriers such as walls or obstruction of network signals by strategic placements.
- It is a cost-saving device. Instead of creating an entirely new network, you can extend the existing network at a cheaper cost.
- Repeaters increase or amplify signal strength.
2. Hub Network Device
A hub is a network device that is used to connect multiple computers together in an internal network. It is similar to a repeater as they both operate at layer 1 of the OSI model. A hub is a dumb device; it does not filter data traffic before sending them. When a hub receives data on one port, it copies the data and broadcasts it to all other ports in the network. There is no data filtration or discrimination on which port should receive the data, all ports in the network receive a copy of the data.

Hubs have multiple ports that can be used to connect multiple devices to the network. All devices connected to a hub are automatically in the same subnet, there is no intelligence in a hub. The data transmission mode in a hub is half-duplex, i.e. data transmission can only occur in one direction at a time – not simultaneously in both directions. They are less expensive, easy to install and maintain, and are efficient in transmitting broadcast messages.
Limitations Of Hubs Compared To Switches
Hubs have limited capabilities when compared to a switch. Switches are intelligent, they actually read the information in the data frame to make a decision on where to send the frame. Hubs do not. The limitations of a hub compared to a switch are as follows;
- Hubs cannot send private messages (they only do broadcasts), but switches can.
- Hubs have very limited security, data can easily be compromised by connecting to a port. Switches offer better security. You can configure more sophisticated security settings in a switch.
- Hubs only support a half-duplex mode of data transmission, collisions are common and the network is generally slower. Switches can support both half-duplex and full-duplex. There is less collision and less congestion in the network using switches.
Rare Use In Modern Networks
Hubs are used to connect multiple computers to the network. They are cheaper than switches and can provide a convenient way to connect multiple devices to the network. However, since a hub floods the data it receives to all ports in the network, it poses a security challenge. All devices in the network get a copy of the data. It is therefore rarely in use in modern networks. Also, it results in unnecessary wastage of bandwidth as it generates multiple copies of data that it will send to all ports.
You use Hubs to connect devices in a local area network LAN.
3. Bridge
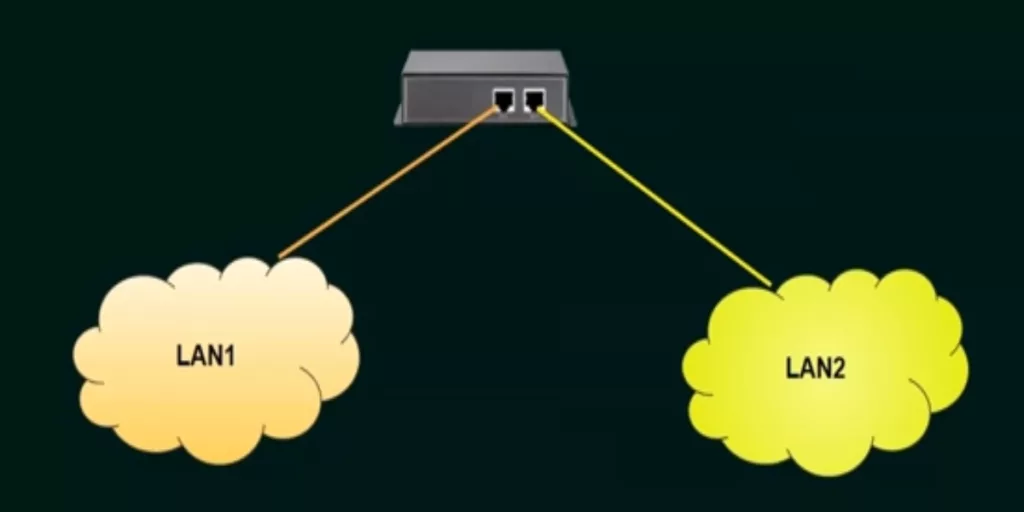
A Bridge is a network device that is used to aggregate different LANs into a single network. A bridge is also a repeater with the additional functionality of being able to read Mac -addresses. It differs from a switch in that it learns about Mac- addresses by using Software while a switch uses special ASIC hardware. You can think of a Bridge as an intermediary between a Hub and a Switch. They are much more intelligent than Hubs but less than a Switch. Bridges operate at the Datalink Layer (Layer 2) of the OSI model. Sometimes, layer 2 switches are interchangeable with bridges.

Like Hubs, Bridges do send out broadcast messages but such broadcasts are only limited to a single broadcast domain. It aggregates the different LANs into a single one so that they can share resources.
A commonly used Bridge is the Wireless Bridge, which is employed to extend Wi-Fi networks. They are used to connect two LANs from different locations into a single network.
Types Of Bridges
There are two types of Bridges, These are Transparent Bridges and the Source -Routing Bridges.
1. Transparent Bridges
Transparent Bridges are “transparent ” to the stations, that is, the stations or nodes are unaware of their presence in the network. They learn and maintain a Mac address table to know where to forward traffic. It means there is no need to do any configurations at the stations for the bridges, even if the bridge is added or removed from the system. Transparent bridges are usually in Ethernet networks.
2. Source Routing Bridges
The Source Routing Bridges are “visible” to the Stations. The Stations or nodes pass information to the Source Routing bridges on how frames are to reach their destination. Source routing bridges make of the MAC destination address of a frame to direct it by the source routing algorithm. The routing information is a part of the frame itself. Token Rings networks use Source Routing bridges.
Uses Of Bridge In A Network
- Bridges are used to extend the range of a network
- Bridges can also combine two LANs into one so that they can share resources. Useful for offices with networks at different locations.
4. Switch
A switch is a network device that is used to forward network traffic within a local area network (LAN). It provides wired access to a network. They operate at layer 2 of the OSI model. Normally, you will not connect your PCs directly to a network, you use a switch to do that. Switches have a lot of interfaces or ports to which you can connect your end devices. Unlike hubs, switches are intelligent devices. They learn MAC addresses, maintain a MAC address table, and forward traffic (ethernet frames) based on MAC addresses.

Types Of Switches
There are two types of Switches, Unmanaged and Managed Switches.
Unmanaged switches – These are very simple switches that do not require configuration (they lack a console port). They provide ports for you to plug in your end devices. Unmanaged switches are ideal for small networks such as those in a home or small offices. They are cheap and easy to manage. The disadvantage of unmanaged switches is that you cannot configure them to perform additional functions such as creating VLANs, Quality of Service (QoS), Port security, etc.
Managed Switches – are much more complicated and are suitable for enterprise environments. You can configure them to meet specific needs of your network e.g. Security, VLANs, QoS, Access lists etc. Managed Switches are more expensive and will require some skill to configure them.
Features Of A Switch
There are a wide variety of features for switches which make them suitable for different requirements of the network. Some of these features are as follows;
- Number of Ports or Interfaces – Switches have a number of ports (unlike routers) that you can use to connect end devices to the network. The common number of ports is 8,12,24, and 48 ports.
- Uplink Ports – Some switches have groups of ports that allow the plugin of Small Form Factor Pluggable transceivers. These are for Fiber Optics cables over long distances and at high bandwidths.
- Virtual Local Area Networks (VLANs) and Quality of Service (QoS) – Most enterprise switches (managed switches) are able to demarcate network traffic at layer 2 by creating VLANs. This can enhance privacy within the network. QoS prioritizes network traffic, especially during network congestion.
- Bandwidths/Speed of Ports – Modern switches are able to achieve speeds in the order of gigabytes per second. Speed is an important performance characteristic of networks. Older switches are slower at 10 megabytes/sec.
- Power Over Ethernet – This is a feature that allows you to power the switch over an ethernet cable. It is very useful in places where it is impossible or difficult to power the device through conventional means.
- Switch Stacking – This is a feature of some switches that allows you to combine multiple switches into a single stack (with more ports) by connecting them with each other. You can then manage the stack of switches as a single unit. It is very useful in creating redundancy in the switch stack. When one switch goes bad or fails, others in the stack can act as a failover.
- Routing Capabilities – Some switches have routing capabilities, i.e. can transmit data across different LANs and over the internet. These are hybrids of a router and a switch. They are Multi-Layer Switches or Layer 3 Switches.
Uses Of Switches
- Switches connect devices within the local area network LAN.
- Switches can be configured to perform special functions, such as dividing the network into sections (VLANs), QoS to prioritize network traffic, or running other networking protocols.
- Switches are points to implement certain security features
- Some switches have routing capabilities (multilayer or layer 3 switches)
5. ROUTER
A Router is a networking device whose primary function is to move data packets between different networks. They operate at layer 3 of the OSI model. (switches and bridges operate at layer 2). A router gives you access to the internet – which is a collection of different networks. It connects different LANs together and allows network traffic (or packets) to move across them. Routers can therefore cover a wide area network (WAN).

Routers forward network traffic using the destination IP address. They maintain a routing table and use it to determine the path to send the network traffic through. When a router receives a packet, it checks its destination IP address and then compares it with entries in its routing table to know which interface it should send it out of.
Oftentimes, there is more than one possible path to the destination, a router will have to make a decision on which path to use to reach the destination. This process of selecting a path for the data packet is called Routing. There are many protocols (sets of rules) or routing protocols that a router uses. Some of the common routing protocols are BGP, OSPF, EIGRP, etc.
Characteristics of Routers
- Routers typically have fewer ports or interfaces than switch
- They provide connectivity between LANs.
- They provide access to the internet.
- Routers run different routing protocols to determine the path to use to reach a network.
Uses of a Router
- To forward network traffic between different local area networks
- To connect devices to the internet
- To implement certain security procedures for the network.
6. Modem
A Modem is a device that converts a signal from one form to another. As a networking device, a modem will convert analog (continuous electrical) signals it receives from the Internet Service Provider (ISP) to a digital form (discontinuous electrical bits of 1s and 0s) that your computer can read and understand. A modem is what brings the internet service from your ISP to your network. It demodulates incoming analog signals and modulates outgoing digital signals from your network to the ISP.
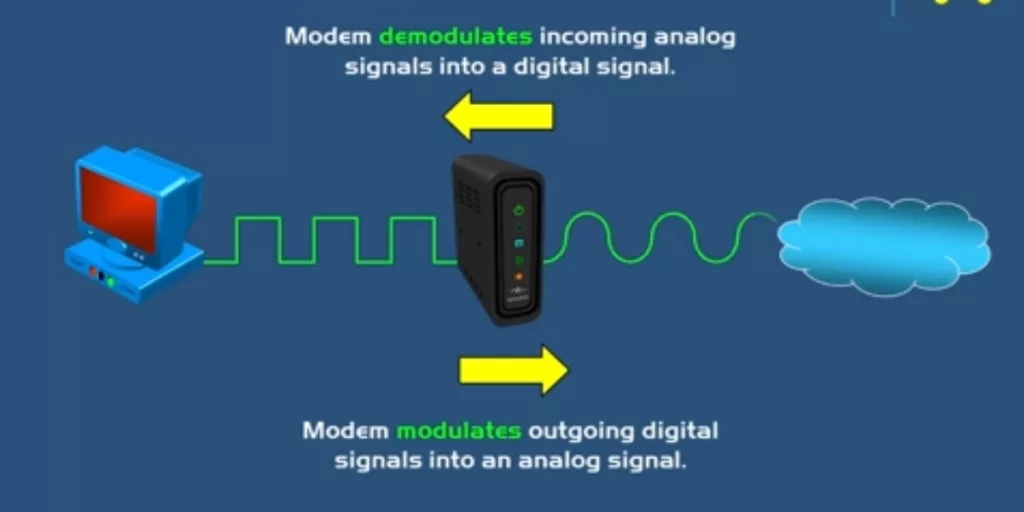
After the Modem demodulates signals from the internet, it passes it on to the router on your network to forward network packets to your LAN(s). For Small Office and Home networks, it is possible to have the modem incorporated within your Wireless Network Router. For more complex networks, a separate device will act as the Modem.
Types of Modems And Distinction Between Them
The common types of modems are Digital Subscriber Line (DSL), Cable, and Fiber Modems. DSL Modems provide internet service by connecting to a telephone line. DSL uses a coaxial cable for connection. Cable Modems are provided typically by the same companies that provide you with cable TV. You connect to the cable network using coaxial cable. Cable modems are faster than DSL.
Fiber modems are modems that receive internet signals via fiber optics cables. These are presented as optical signals which are then transformed into electrical signals. They are very fast and more efficient than DSL and Cable modems.
7. Firewall
A Firewall is a specialty network security device that controls network traffic entering or exiting a private network. A firewall will prevent unauthorized access to your network by filtering traffic based on certain criteria such as IP addresses, port numbers, domain names, protocols, programs, or even keywords. They help keep your network safe from unauthorized access usually by bad actors. They are essential components of any network security architecture.

It is important to note that firewalls can be standalone hardware devices usually for large enterprises (e.g. Cisco ASA firewall, Firepower 2100) or they can be built-in components of other networking devices such as routers. They can also be software end devices such as your PCs or part of a Cloud Infrastructure.
A network or security administrator will usually configure firewalls to allow or restrict certain traffic types. For example, by implementing Access Control Lists (ACLs). You must configure firewalls using firewall rules. Also, you place them at strategic points in the network to filter traffic. e.g. Inside the network before your routers or Outside the network before the traffic reaches your router.
Modern firewalls also have some advanced features incorporated into them like Intrusion Prevention Systems (IPS) and Intrusion Detection Systems (IDS) which enhance the capabilities of the firewalls. These types of Firewalls are called Next-Generation Firewalls. IPS blocks certain traffic types while IDS warns you of incoming malicious traffic so that you can take additional precautions.
Types Of Firewalls
Firewalls can either be Host-Based or Network-Based Firewalls.
Host-based firewalls are software that is installed on individual end devices to protect them from malicious attacks. Most common Anti-virus have inbuilt firewalls to protect your system. Common examples are the security programs pre-installed on your computers. Sometimes, Host-based firewalls are available through third parties e.g. Zone Alarm.
Network-based Firewalls are placed between networks or between your private network and the internet. They offer protection for the entire network. It can be a combination of both software and hardware devices. Network-based Firewalls are very important, especially in large networks. Most organizations will implement both host-based and Network-based firewalls to achieve robust security of their network.
Characteristics Of Firewalls
- They control and monitor traffic based on Firewall rules (configured rules)
- They can placed “inside” or “outside” your network before traffic reaches your router to filter traffic
- They can be Host-based or Network-based.
- Next-generation firewalls include more modern packet filtering capabilities – Intrusion Detection Systems IDS and Intrusion Prevention Systems IPS.
Use of Firewalls
- Network Security – This is the main function of a firewall in a network. It prevents bad actors from compromising your network.
- Access Control – Firewalls are also used to filter who can access certain resources in your network. It also makes sure that certain resource or information does not leave your private network.
8. Network Interface Card (NIC)
A Network Interface Card (NIC) or network adapter is a piece of hardware device that allows you to connect networking devices to the network. Most modern networking devices have the NIC built-in to the device. Each NIC has a unique MAC address. Some devices may have more than 1 NIC card to provide connectivity to a network. Every Network interface card is also characterized by a specific network speed for the interface and can be upgraded.
The NIC will have ports that you can use to connect devices to the network. The most common of these are the RJ45 ports which use ethernet cables to connect the network. Other types of ports are SFP, LC, and GBIC which are used for fiber optics connections.

Types of NICs
NIC can be either be internal or external. Internal NIC are a part of the networking device. For many devices , there is a slot connected to the motherboard where you can slot the NIC.
External NIC are for devices that do not have a built in NIC card. They are external to the networking device. The common one is tge Wireless NIC for Wireless connectons. You can also adapt them for different network ports to allow connectivity a network.
Conclusion
Networking devices are hardware resources that help you build a network infrastructure for the transmission and sharing of data. The common network devices include repeaters, hubs, bridges, switches, routers, firewalls, etc. Repeaters and hubs are dumb devices that function to extend the range of the network, Bridges aggregate two LANs into a single network. Switches are smart devices with a lot of ports to connect end devices to a network. Routers connect different LANs and help you connect to the Internet, Modems function to convert analog signals from the Internet to digital signals that your network can understand, and Firewalls secure the network from unauthorized access.
Basic foundations on how these networking devices work are an essential component in learning about networking.
Read




