Introduction
We live in a world of interconnected devices, from smartphones, tablets, and computing devices to machinery and infrastructure used to run modern industries and businesses. They form a network of devices that support businesses and enrich our personal lives. Sadly, however, there is a wide array of cyber threats that are designed to cause harm and disrupt activities. It is important to be aware of these challenges and take steps to protect your infrastructure against them. This blog post will explore the essentials of Network Security and practices for protecting your infrastructure.
This will be useful, whether you are a seasoned IT professional willing to start developing and adopting security skills to improve your infrastructure or you are a curious novice willing to learn the basics.
Why Does It Matter?
Businesses and organizations must take steps to secure their networks as the losses due to cyber-attacks can be substantial. According to Statista, the global estimated cost of cybercrime in 2022 alone is $7.08 Trillion (projected to reach $8.15 Trillion in 2023). Losses can range from direct financial losses, aiding frauds due to leaked sensitive data, disruption of critical business infrastructure, reputational losses, loss of critical data, Ransom payments, clean-up costs, etc.
Another research found that 61 percent of organizations experienced at least a 25 percent increase in cyberattacks since 2020. The number of bad actors is certainly on the increase and they are becoming much more sophisticated. It is important to learn the essentials of Network Security and measures to protect your infrastructure from cyber attacks.
Fundamentals of Network Security


Network Security relies on some fundamental concepts, these are concepts a Network security expert must be familiar with to secure the network infrastructure properly. We discuss some core network security essentials below;
The CIA Triad
The CIA Triad is an acronym that stands for Confidentiality, Integrity, and Availability. They serve as a working framework or checklist against which you can measure the effectiveness of any design, implementation, and assessment security measure. Any failure in any of these core concepts signifies a breach or compromise of the security of the Network. The different elements of the CIA triad are as follows;
1. Confidentiality
To fulfill the quality of confidentiality means that only authorized persons have access to a piece of data or the Network. It assumes that information that an organization can keep certain sensitive information private and is only accessible to authorized persons. Confidentiality of Information can be achieved with two main technologies; Access Control and Encryption. Access Control comprises Authentication which answers the question of “Who is accessing this data?” and Authorization which addresses the question of “Are you allowed to do this or not?”
Authentication uses tools such as Multi-Factor Authentication MFA while Authorization uses Role Based Access Control RBAC to determine what you are allowed to access or privilege. Encryption is the technology that scrambles data in such a way that it can only be read by someone who has the cryptographic key to unscramble (unencrypt) the data.
2. Integrity
Integrity is the quality that states that a message is true to itself and that it has not been altered, added to, or modified in the course of a transaction or transmission. It determines whether or not you will trust a message to be a true representation of its original state. If there has been a change or has tampered with it, you can discard it so as not to cause damage. Some technologies that allow us to ascertain the integrity of a message are Digital Signatures and Message Authentication Codes (MAC).
Both Digital Signatures and MAC are both cryptographic functions. When a hacker attempts to tamper with data, it will carry with it the wrong Digital Signature or Faulty Message Authentication Codes, and as such, it can be detected and then treated as untrusted, and discarded.
3. Availability
Availability is the quality that indicates that authorized users can access data or network resources when they need to. Data, applications, or networking resources are only valuable to an organization if it is available for use. It is common for hackers to disrupt the availability of the system if they cannot attack the confidentiality or Integrity. Oftentimes, the tool of the hacker is designed to overwhelm the system with fraudulent requests in a way that depletes the resources or the ability to respond to legitimate requests. Some ways these attacks include Denial of Service, Distributed Denial of Service, Syn Flood Attack, DNS Amplification attack, Reflection attack, etc.
You mitigate against these types of attacks by implementing a time-out mechanism for requests and making use of packet filters and firewalls to identify and block traffic from malicious sources.
Threats And Vulnerabilities
Threats describe anything or action that could exploit the weakness (or vulnerability) in a system. They are carried out by bad actors (Threat Actors or Hackers) attacking the confidentiality, Integrity, or Availability of your systems, network, data, people, applications, and more. Common Threats are Malware, Ransomware, Phishing attacks, etc
Vulnerabilities refer to the weaknesses in the system. Something bad actors can take advantage of; to cause harm. It could be a procedure, personnel, codes, or flaws in the infrastructure, databases, or software. etc. Vulnerabilities in themselves alone are not much of a problem, but they can be used to do damage. Fixing a particular vulnerability is called a patch.
Risks are the likelihood or probability of an attack taking place. Risks quantify this likelihood, the cost implication of the potential damage that could result from it, and the frequency of the exploit taking place. It is very important to quantify risks and take counter-measures or Controls to reduce their impacts.
Risk Assessment
Risk Assessment is the process of identifying vulnerabilities in your IT infrastructure, characterizing and assessing them for the danger they pose, and implementing key security controls to mitigate against them. It helps you identify the risks and help you prioritize them based on the cost implications and the available resources. It is impossible to eliminate risks, you can however deploy controls or counter-measures to improve your network security. Some steps in the Risk Assessment process are as follows;
1. Scoping
This defines the context and objective of the Risk Assessment. Scoping sets limits on what you want to focus on at the moment e.g. The Website and Applications of the organization. In this case, you wouldn’t have to worry about the physical security of devices or personnel, those will be the scope of another assessment.
2. System Characterization
The system characterization identifies all the assets, procedures, data, systems, etc that are in the scope of your risk assessment. It involves getting a better understanding of all the components in the environment of what you are assessing. System characterization also includes making a data map that shows how data enters and leaves your system, data inventory, vendor inventory, etc.
3. Identifying Threats and Vulnerability
Identify the threats and vulnerabilities that exist in the environment that you have characterized. Make use of Threat catalogs such as those provided by the National Institute of Standards (NIST) and Health Information Trust Alliance (HITRUST), to see which apply to your environment. Both NIST and HITRUST provide Cybersecurity Frameworks for making comparisons. Other tools you can use to test vulnerability are audits, penetration testing, vulnerability scans
4. Analysis of Vulnerability and Existing Controls
Make a list of all the vulnerabilities in the systems that you have identified as well as all the existing controls that are already in place as counter-measures. Identify things like the antivirus, firewalls, access controls in place, security configurations, trained security personnel, security policy and procedure in place, etc.
5. Assess the Potential Impact and Likelihood of Its occurrence
Make a comprehensive analysis of the potential impact of each of the threats you have identified in terms of cost and resources to the organization and the likelihood of such a breach taking place. Make a quantitative evaluation for each threat identified.
6. Prioritize Risks And Recommend Controls
Prioritize the risks you have identified based on their severity and likelihood. Recommend Controls to mitigate against the risks you have prioritized to the management of the organization. This is usually after you have checked them against the existing controls you have identified earlier.
7. Document Findings and Recommendations
Make a detailed recommendation of your Risk Assessment and recommendation to management for implementation and future reference. Such documentation can be helpful when making future updates on your Network Security.
Building A Secure Network Architecture


A Secure Network Architecture implies that you design your network in a way that is resilient to cyber-attacks and that secures your networking infrastructure. The following are core considerations in building a Secure Network Architecture.
Design Principles
The design of any Network Architecture must incorporate the following security principles for it to be resilient and secure against cyber attacks, these principles are as follows;
1. Defense In Depth
Defense in Depth demands that you have multiple security mechanisms for any design or that no network or system set relies on a single security mechanism. This means that there is no single point of failure on which the entire security apparatus depends. You create multiple barriers or obstacles for the intruder, and if one of such fails, the system is still secured with other measures at different levels, independent of the security at other levels.
For example, in a typical modern network, end devices will require multi-factor authentication (MFA) at end devices just to sign in to the network, Security policies at the network links to only allow only certain types of traffic, an Antivirus to keep corrupted payloads out, firewalls at the server applications, encrypted data at the database, etc.
2. Least Privilege
The least privilege principle means that you only give access to users to the extent they need it and only for as long as they need it. It implies they will have a limit to what they can access with the network. This also compartmentalizes access, for example in an organization, the finance database is only accessible by those within the finance department. The principle of least privilege also demands that services or protocols that are not needed in the network are shut down or disabled, including shutting down unused ports, removing users who are no longer in the organization, disabling protocols, removing hardware not used, etc.
Another aspect of Least privilege is Hardening the system, which involves changing all out-of-the-box configurations of networking devices, and changing the default passwords, and usernames. Hardening the system makes it much more difficult for hackers and intruders to have unauthorized access to the networking infrastructure.
3. Separation of Duties
Separation of Duties ensures there is no single point of control in your security setup. Every request made by a user will need approval from some other user. No single person can initiate and then authorize the same request. If a request is coming from some bad actor, it will need to pass through another system of authorization. It forces collusion of at least more than one bad actor for there to be a successful compromise to the network.
It is like having a door with two separate sets of keys. To access the resource behind the locked door (e.g. funds, database, critical infrastructure, etc), you will need the collusion of at least two parties to unlock access. Separation of Duties (or Dual control) is common in a most well-structured environment and is a good design principle to reduce security risks associated with a single point of control.
4. Secure By Design
Security is not an afterthought or an added feature to the design of a network. Secure by design means building and embedding security features at every stage of designing a network, from designing it, using secured codes free from bugs, proper installation of devices, testing on a secured platform, and then finally at the production stage. This helps in building a system that is relatively secure right out of the box.
Secure by design implies also that the security responsibility is everyone’s responsibility. Security considerations are in place from the designer to the administrator and then to the final users. The best security architectures are those that are multilayered and built-in at every step.
5. Keep It Simple Stupid -KISS Principle
The Keep It Simple Stupid is a Network design principle that states that you should avoid making a system harder or more complicated than it is necessary. The goal of the KISS principle is to make security easy to implement for legitimate users and difficult for intruders. If a system is unnecessarily difficult for the intended user, they will end up engaging in risky practices.
A common example of this is in the implementation of password requirements. If the password complexity is set to be too high, people will start storing the passwords on the same device. This in essence will defeat the purpose of having a password at all. Avoid designing a system to be more complex than it needs to be. Complexity gives more room for the hacker to potentially cause harm and for legitimate users to abandon healthy security practices.
6. Avoid Security By Obscurity
This is in essence what you should necessarily AVOID doing when designing the security of your network. You should avoid using an obscure system, where only the inventor can tell how it works. There should be no black boxes or algorithms which you can tell or see how it works. Such “secrecy” is a potential risk to the security of your infrastructure. Use systems that are transparent and secure such as public key cryptography and follow the security guidelines associated with it.
Secure Network Topologies
A part of the process of protecting your Infrastructure is to build secure networking topologies. Secure Network topologies refer to the arrangement and structure of networking components to minimize vulnerabilities and protect against potential threats. Enterprise Network will consider the following to build secure network topologies;
- DMZ (Demilitarized Zones) – DMZs are created to host external users who want access to an organization’s resources such as web servers. Instead of allowing such access directly to internal resources, a DMZ is created and those resources are placed there. It adds a layer of protection by isolating potentially risky external traffic.
- Firewalls, Intrusion Detection and Protection Systems (IDPS) – These are systems/devices at the network’s edge to help monitor incoming traffic. They alert you when there is a suspicious traffic. They form perimeter security at the edge of the network
- Intranet– Private Internet that is only accessible by the internal staff of an organization. It blocks external users from the internet. Intranets are only accessible through the private network or by VPN
- Guest Networks – You create Guest Networks to provide only internet access to external users. Such internet access is on a separate network, ideal for visitors during meetings or presentations. It does not grant access to the internal network. It helps keep an organization’s internal network from unnecessary risks from visitors.
Secure Communication Protocols
As part of enhancing the security of your networking infrastructure, it is essential to implement secure communication protocols. It ensures the confidentiality of sensitive data at all times. You can achieve this by using Encryption technologies and Virtual Private Network (VPN).
A. Encryption Techniques
Encryption Techniques rely on scrambling data in order to keep them confidential. Encrypted data can only be read by the intended recipient. Two common security technologies you can implement to secure your network are Secure Socket Layer/Transport Layer Security and IPSec
1. Secure Socket Layer /Transport Layer Security SSL/TLS
SSL/TLS are cryptographic protocols that are used to encrypt communications between a client and a server. They are implemented through a web browser or web application. SSL is the predecessor to TLS. They both use symmetric and asymmetric encryption. It ensures that sensitive information is protected from interception in the course of transmission (Integrity and confidentiality).
2. IPsec
IPsec is a framework of open standards for ensuring secure communications over IP Networks. It is a network layer security that works by creating a secure tunnel between two nodes for communication. It uses Encapsulating Secure Payload (ESP) for encryption while Public Key Infrastructure (PKI), and Digital Certificates for Authentification. You can use IPSec for securing device-to-device, device-to-subnet, and subnet-to-subnet communications.
B. Virtual Private Networks (VPNs)
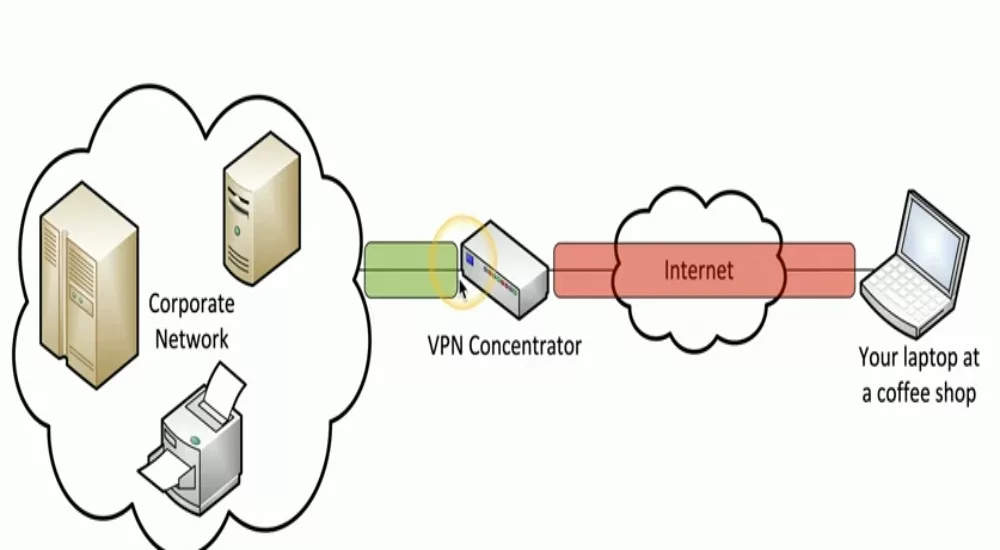

Virtual Private Network is a way to send data securely over the public internet(untrusted network). VPN allows you to send data between two points through a secure tunnel. At the heart of the VPN is a concentrator that encrypts/decrypts the data. Integrating a firewall with the concentrator is a common practice to improve network security. VPNs can allow you to access a private network securely and remotely. The installation of VPNs is often on end devices.
You access the VPN concentrator of your organization through a secure tunnel over the internet. The Concentrator links directly to the private network. Virtual Private Networks help you achieve privacy and security as data sent over the public internet is through a secured tunnel.
Authentication And Access Control


Authentication and Access Control are essential components in protecting your networking infrastructure. They are control measures to ensure that only authorized persons can access your networking resources. They form part of the frontline defense. Authentication validates the identity of users, while Access control determines what resources they can access. Authentication and Access control will help keep hackers at bay when adequately implemented.
User Authentication
Authentication of users is by using Password Policies and Multi-Factor Authentication
1. Password Policies
Password policies describe the set of rules that govern the creation and management of passwords. Implement a password policy that is user-friendly and at the same time good enough to keep bad actors out. Mandatory password change at intervals improves the security of the network.
2. Multi-Factor Authentication (MFA)
We use Multi-factor authentication to authenticate the identity of a user by using at least 2 verification factors. It provides an extra layer of security to the user’s account and to the organization. It combines at least any two verification factors from the category of “something they know” (e.g Passwords, secret id, etc), “something they have” (e.g Yubikeys, 2FA installed on the device, swipe card), or “who they are”(e.g their fingerprints, retina scan, etc).
Access Control Models
Access control determines “who is allowed to access what?” It is a security policy that gives the right or authorization to access a resource. The enforcement of those policies ensures that only authorized persons gain access. The process of determining those rights is called Policy definition and can be achieved through the models below;
1. Role-Based Access Control (RBAC)
Role-Based Access Control grants rights to users based on the roles they perform in the organization. The rights is in the Roles. Scaling is easy with RBAC as there is the provision of the rights in the roles. Where there are clear demarcations of roles, create an RBAC for the different roles.
2. Discretionary Access Control (DAC)
Discretionary Access control grants rights arbitrarily based on the discretion of the Administrator. It is very flexible, however, can be difficult to do on a large scale as it is often prone to errors. There are no standards for granting rights to users. The administrator can inadvertently grant access since there are no clear rules for granting rights.
3. Mandatory Access Control
Mandatory Access Control grants access based on the security clearance of the user. It uses labels to indicate security levels. Users can only gain access to information that corresponds to their security clearance level. The higher your clearance level, the more sensitive information you can access.
NETWORK SECURITY BEST PRACTICES


It is important to know that securing your infrastructure is an ongoing process. Hackers are always evolving, new vulnerabilities are constantly being discovered, to keep pace with security demands, it is helpful to implement the following security best practices;
1. Regular Audits and Monitoring
Conduct regular audits to review existing security measures and ensure they align with policies and standards. Assess all configurations, access controls, personnel, security procedures, vulnerabilities, etc. You may need to implement new solutions to fix new findings. Conducting regular audits helps you keep your security implementation up-to-date and fix lapses that may appear from time to time. It is also very important to constantly monitor your network activities in real-time for signs of potential threats.
2. Patch Management
A patch is a change in software to fix bugs, close security holes, or add features to a program. They are a fix to a security vulnerability. Patch management is identifying, acquiring, testing, and installing. It is an important aspect of your network security and also a regulatory requirement in many cases. Software companies will often release patches to fix vulnerabilities as soon as they become available. It is important to implement patches as soon as possible. Unpatched systems are vulnerable to hacks
3. Incident Response and Recovery
Security is a combination of prevention, detection, and response. It is important to make provisions for response in case of a security incident. The average Incidence Response time is 67 days, One of the ways to cut down the cost of a security breach is to have a good incidence response capability. The traditional approach consists of isolating the incidence in order to contain it, doing a triage, and then a remediation to fix the breach.
A much more modern approach is to use SOAR (Security, Orchestration, Automation, and Response) which is an automated approach to reduce the recovery time.
EMERGING THREATS AND TRENDS
The security landscape is constantly changing. It is essential to be aware of the emergence of new threats and prepare to handle them. Some of the common categories are as follows;
1. Malware and Ransomware


Malware is software that has been installed in your system with malicious intent. They can be used -sometimes unbeknownst to you – to gather sensitive information or even bring down the security of your network. They range from viruses, spyware, worms, rootkits, trojan horses, etc. It is important to guard against them, keep your operating systems updated, patch vulnerabilities, use anti-malware, etc.
Ransomware is a class of malware that hackers use to deny you access to networking resources or data. They do so by encrypting (using cryptographic keys) your data and then demanding a ransom to restore it. It is often difficult to unencrypt them. Always keep a backup of all your sensitive documents and encrypt sensitive data.
2. Social Engineering Attacks
People are the weakest link in any security infrastructure. Hackers can leverage this and launch a Social Engineering attack. It involves manipulating people to divulge confidential information, perform actions, or compromise security. Some forms of Social Engineering attacks are Phishing emails, Pretexting, Impersonation, Tailgating, etc. Educate your staff to be aware of the different forms of social engineering attacks and how to avoid them.
Another thing you can do is to block users in your organization from accessing known fraudulent sites. You can do this by using a Secure DNS with Quad9 capability. It blocks access to a list of known phishing sites.
Conclusions
Network Security is an important aspect of the deployment of technology in any organization. It helps protect the organization’s infrastructure from hackers who may seek to cause harm. It will require a deep understanding of the core security fundamentals and implementing a multi-layer approach. Standard security practices include conducting a risk assessment to identify the threats and vulnerabilities in the system, designing your network security architecture based on security principles, and implementing different network topologies to address different challenges.
Others include using secure communication protocols, encryption technologies, Authentication and Access Control, and implementing best security practices. Finally, it is important to be aware of emerging security threats and trends. These include malware, ransomware, and Social engineering attacks, and take steps to mitigate against them. Having a system of robust security at every level.
READ




