You can become a victim of an online scam if you are not aware of some of the basic setups for an online scam or if you ignore the red flags that are common to all online scams. We will consider a specific type of online scam called Phishing attacks because they seem to be the prevalent type you may have even common across. We will look at things that will help you identify a phishing attack and how you can protect yourself from them.
What Is A Phishing Attack?
A phishing attack is a type of social engineering where a fraudulent message is sent to a target on the premise that it is arriving from a trusted source. Its basic purpose is to trick you (the victim) into revealing sensitive information such as passwords and payment information that a hacker can use to steal from you. A phishing attack will often involve you receiving some kind of message via text, email, phone call, social media account, etc, and a request for you to perform some actions or give away some information that eventually leads to your data compromise.
Phishing attempts fraudulently to coerce or encourage you or an innocent victim to provide personal information or business information, not limited to but usually including account information like user names and passwords or other personal information, whether it be credit card numbers, phone numbers, addresses, bank information, social security numbers, etc.
Who Is At Risk?
Everyone is at risk of a Phishing attack. If you have ever received an unsolicited email, text message, (or even a phone call) from some random unknown person claiming to be from your bank, insurance company, etc with an offer to help you fix some purported problem with your account and then request that you click on some links (that look like your bank sites with some slight variations)to fill in your details, etc, chances are high that those were phishing attempts.
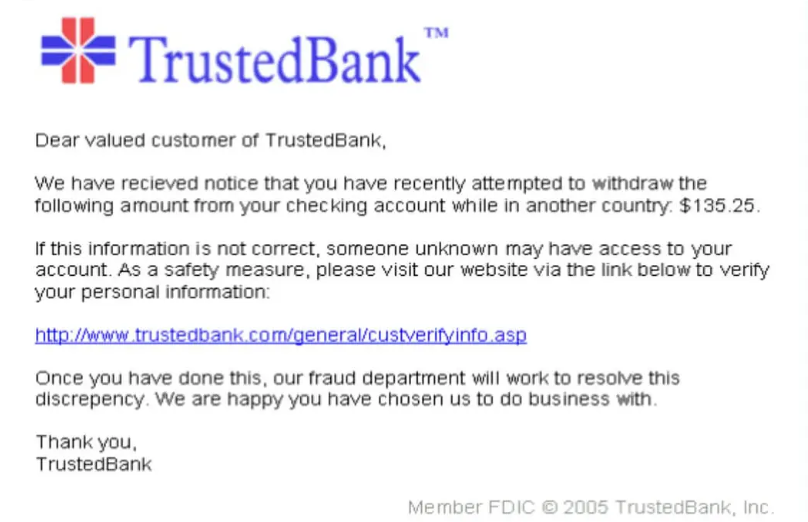
An example of a Phishing email. Source: https://en.wikipedia.org/wiki/Phishing
According to a survey released by the UK Office for National Statistics, 3 percent of persons who received a suspected phishing email, clicked or replied to the phishing email. 11 percent of those who replied provided information that could be used by the fraudsters to compromise their accounts. The same report also showed that adults aged between 25-44 years were more likely to receive phishing emails.
Given that phishing messages can be sent in bulk with very little cost to the scammer, it seems we are going to be dealing with this problem for a long time. Hence it is important for you to learn how you can identify them and then protect yourself from them. You must know the difference between a legitimate message and those from foes i.e scammers/fraudsters
How Do I Identify A Phishing Email Or Message?
There are a couple of things that can help you identify a Phishing message. As a rule of thumb, you should check all your messages for the following Four characteristics. They will guide you on what to do next.
1. Does It Contain A Link?
Phishing messages from whatever source (text, emails, social media, telegram, etc) usually will contain a link to a phishing site that is masquerading as a legitimate site (e.g your bank site), it will often prompt you to log in with your details such as passwords, username, pins, credit card number, social security numbers, etc, unbeknownst to you that you are on a wrong site. They can then steal your sensitive data and use it to log in to a legitimate site.
2. Does The Email Contain An Attachment?
A phishing message may contain an attachment or file. You will often be required to click on these or download them. The file can be a fake document such as some contract agreement, summons, etc. Alternatively, it could be malicious software (Malware) that will automatically download and install on your device the moment you click on it. Malware will compromise your device and steal your sensitive data which can then be used to steal your funds(for example). It is best practice NEVER TO CLICK on links in an email unless you have verified the authenticity of the source.
3. Is The Email Requesting For Any Information?
Sometimes fraudsters can be more direct in requesting sensitive information in the guise of trying to help you solve a particular problem related to your account. The sender may be disguised as someone you are familiar with, a friend, a business partner, your bank, or someone you feel you can trust with such information.
4. Is It Asking Me To Contact Someone Else?
The message may require you to contact somebody( via email, phone number, etc) who in essence will devise some crafty ways to coerce or entice you to submit your data.
What To Do If The Message Contains Any Of The Above
If the message does not contain any of the above 4 listed characteristics, it is safe to pass them as not phishing. If however, the message contains one or more of the listed characteristics, you can then inspect them further for the following red flags.
Common Red Flags Of Phishing Messages
1. Errors
This is a common feature of messages fraudsters. They are always in a rush to reach as many potential victims as they can. They will oftentimes pay less attention to errors. A legitimate email from a legitimate business will scrutinize the emails they send to clients and make sure they are professional in their correspondence. The presence of errors -typos or grammatical- is often a red flag that the message may be phishing.
2. Language And Content
The content of a phishing attack can be bizarre or outright senseless. It could be anything really and often will not make much sense. Some examples may be that you have received an inheritance from a dead aunt from some remote part of the world and you are required to click on a link below to see the details or that you have just won some money from your bank and you should drop your card details in order for them to credit your account.
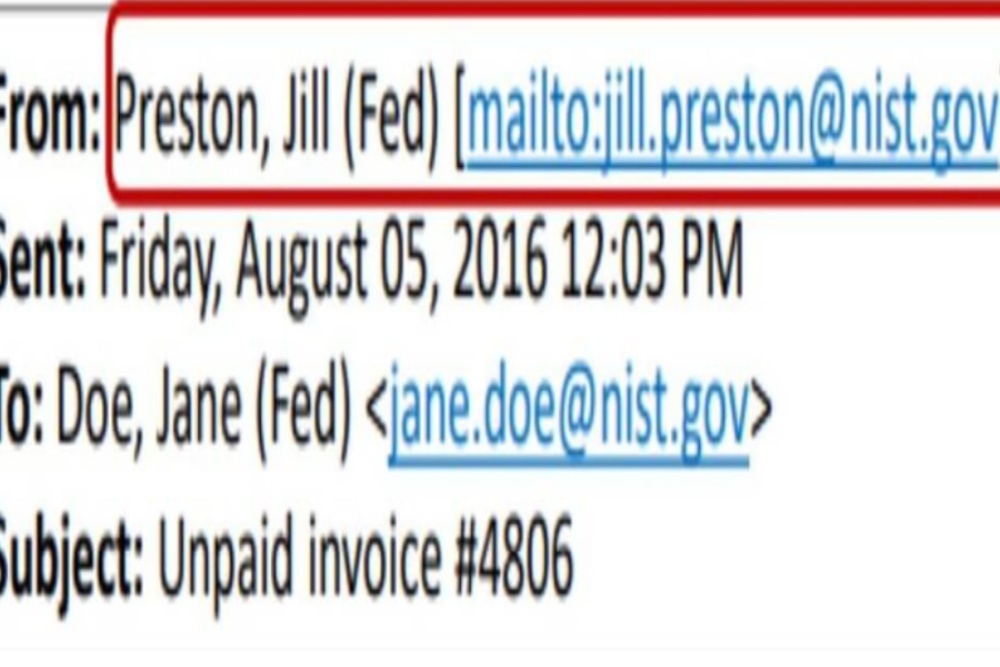
3. Technical Indicators
This is similar to the above and could include wrong titles and positions, technical abnormalities, repetitions, etc. An example is a screenshot below
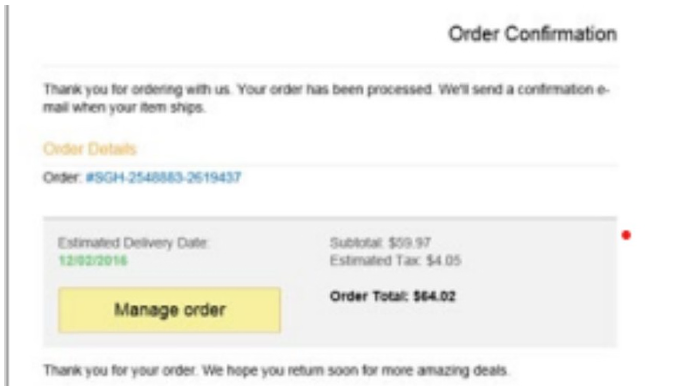
4. Visual Presentation Indicators
Imagine you are getting a shipment notification for an order you never made. The goal is to get you to click on a link that might be malware that can compromise the security of your device.
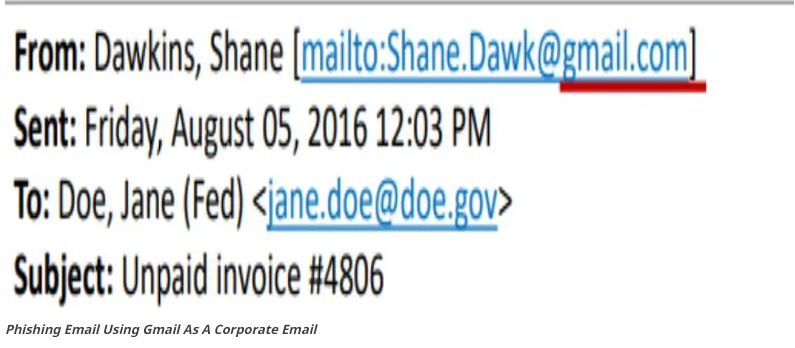
5. Common Phishing Tactics
As a general rule, your bank or Amazon is never going to send you a message using Gmail or Yahoo Mail, nor will a company of reputable standing. Companies will often use their official email. Phishing emails often will the common Gmail or other common mail services. Be sure to check the source of an email and compare them with those from the official site.
Other Common tactics will include
i. A sense of urgency in the message
ii. Special or limited offer
iii. A scare tactic such as the potential of losing your funds if you don’t acquiesce to the request
iv. Mimic a work in progress such as a Customer’s Service desk or support services.
v. Promise of huge fortune or Opportunity
vi. Poses as a friend, family member, colleague, supervisor, or someone with whom you share acquaintances.
vii. Demanding information.
How To Protect Yourself From Phishing Attack
1. Stay Vigilant
Check your messages for things that could make you vulnerable to an attack. Are there links or files attached to the message, are there obvious red flags in the message?
2. Bookmark Sites You Visit Frequently
Bookmark sites you use frequently, including those that have to do with your finances, and always use these whenever you want to access the sites. Never click on links to access these sites. Use bookmarked pages.
3. Invest in Anti-Malware Protection For Your Device
Buy and install anti-malware software that can help you detect the presence of malicious links or downloads and warn you to take extra precautions. It helps to have a good one installed on your device. Search the web, you might even get some for free.
4. Never Click on Unverified Links or Downloads
You should never click on links or download documents online unless you have verified the source as being legitimate. Only proceed after you have confirmed the source. Ideally, you should only use official legitimate sites for downloads rather than those sent to you unsolicitedly.
5. Confirm the Identities Of the Sender When Making Transactions
You may need to use alternative means to confirm the sender’s identity if you get a request for sensitive information. If it is a friend or business associate, call them on the phone to validate the message sent via text or mail.
6. Use Search Engines, Don’t Click on Ads.
Avoid clicking on Ads. They can be fraudulent Ads. Google or ad agencies are not liable for scams that are on their platforms. It is your responsibility to protect yourself from phishing attacks.
A Useful Tool To Check Phishing Attack (Websites)
Here is a website that has a large collection of phishing sites. It currently has over 8 million sites reported as phishing sites. You can check any link against this background. Chances are high that the site is already in the database of phishing sites. You can run a search at https://phishtank.com/
Conclusion
Phishing attacks are socially engineered messages that are designed to coerce or encourage you to release your sensitive personal information to a fraudster unbeknownst to you. It relies on you having some level of trust in the sender of the message. Successful Phishing attacks can result in huge financial and reputational losses. All Phishing messages have some characteristics in common and as such can be used to reasonably identify them and thereby take steps to protect yourself.
What you can do to protect yourself should include knowing the different forms a phishing attack may present. You need to become more vigilant about their presence, be able to spot the red flags, and take measures to protect yourself. Having a list of Do’s and Don’ts such as not clicking on links whose source you have not verified and also having the understanding that you are the last line of defense against phishing attacks.
CREDITS
https://www.nist.gov/publications/can-you-spot-phish
READ




